The origin server stores a website’s or application’s content and data.
As the starting point for all requests made to a website, the origin server’s main responsibility is to access the requested resource from the server’s file system and send it back to the client.
There are two distinct categories of origin servers: public and private. Public origin servers are primarily designed to deliver static content like HTML documents and images. They respond to requests from any client, regardless of their location.
On the other hand, private origin servers serve content exclusively accessible to a predefined group of users. They validate the identity of each client before granting access to the requested resource. Private origin servers are also employed to provide dynamic content, such as database queries and user-generated content.
Key Characteristics of Origin Server
Primary Data Source: The origin server holds the canonical or master copy of a website’s content, including HTML files, images, videos, scripts, and databases.
Content Generation: It is responsible for dynamically generating content, processing server-side scripts (e.g., PHP, Python, or Node.js), and interacting with databases to deliver personalized or up-to-date content to users.
Data Storage: The server stores data in its file system or databases and serves it in response to client requests. This data can include web pages, media files, user accounts, and more.
Security: Protecting the origin server is crucial to prevent unauthorized access, data breaches, and other security threats. Security measures such as firewalls, access controls, encryption, and regular software updates are essential. Here is an insight on six essential techniques for Origin server protection.
Availability: Ensuring the origin server’s high availability is important to prevent downtime. This might involve redundancy, load balancing, and failover mechanisms.
Content Delivery: Sometimes, content delivery networks (CDNs) are used to distribute and cache content closer to users. CDNs can offload traffic from the origin server, improving performance and reducing latency.
How Does Origin Server Work?
Origin servers are critical in the web ecosystem by managing incoming requests and delivering website content to users. Whenever a user accesses a webpage, a request is initiated to the origin server to fetch the required content. The geographical distance between the user and the origin server can cause latency, causing delays in content retrieval.
Additionally, establishing a secure SSL/TLS connection between the user’s client and the origin server introduces extra round-trip time (RTT), which quantifies the total time, typically measured in milliseconds, from the moment a browser requests information to when it receives a response.
Various factors, including physical distance, network congestion, intermediary nodes, and intermediate web servers, can impact RTT.
For website owners, it’s important to regularly maintain and update their origin servers because these servers have a limited capacity. Exceeding this capacity can lead to downtime. When the origin server experiences downtime or slow performance, end users may encounter delays or disruptions in content delivery.
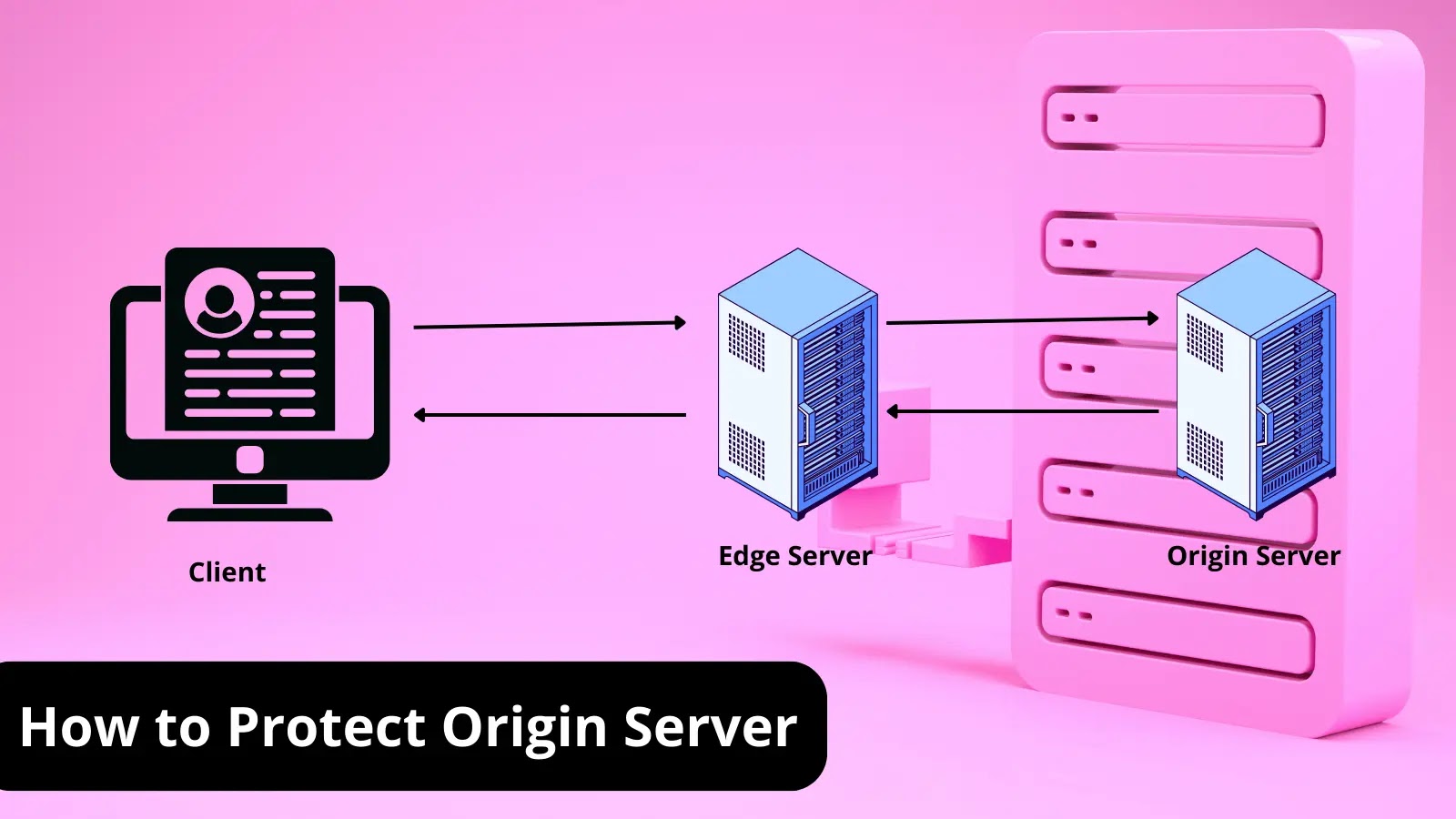
While an origin server can handle all requests made to a website, this approach would be inefficient and unmanageable.
Therefore, most origin servers are configured to delegate specific requests to other servers, such as edge servers or caching servers.
Protecting Origin Servers: Why It Matters?
It’s crucial to highlight the importance of protecting origin servers, given that a server outage has more wide-reaching consequences than a single application’s isolated downtime.
The vulnerabilities that put origin servers at risk include:
Unidentified Applications: Instances of Remote Code Execution (RCE) or Cross-Site Scripting (XSS) vulnerabilities may persist in applications that have been retired but remain publicly accessible. Because these applications coexist on the same origin server, a compromise in one can compromise them all.
Application Weaknesses: An SQL Injection (SQLi) vulnerability in one application can serve as a gateway for hackers to steal data from all other applications residing on the same origin server.
Brute Force Attacks: Attackers may attempt to gain unauthorized access to the origin server by repeatedly trying different usernames and passwords. Strong password policies, multi-factor authentication (MFA), and account lockout mechanisms can help stop brute force attacks.
DDoS Attacks: Even a DDoS attack targeting one application can exploit the server’s resources, causing all other applications to become inaccessible.
How To Protect the Origin Server?
Employing a CDN is one of the effective ways of origin server protection as it conceals the origin server’s IP and distributes incoming requests among edge servers to prevent overload during traffic spikes. It also conducts preliminary inspection of HTTP/S requests, effectively blocking DoS attacks aimed at the origin server and guaranteeing uninterrupted service availability.
Despite the protective benefits a CDN offers for your origin server, it is applicable only for static content and in case your applications have a lot of dynamic content and APIs, it is not possible for CDN to protect origin servers. This underscores the importance of implementing a web application firewall (WAF) and robust security settings on your origin server. Such precautions add layers of complexity for attackers, increasing the difficulty of discovering and exploiting server vulnerabilities.
WAF plays a pivotal role in protecting applications by acting as a protective shield in front of the application. This shield carefully filters and permits only legitimate requests to reach the application, effectively blocking malicious traffic.
However, it’s important to note that, despite the protection offered by WAF— there are ways that could allow attackers to access the origin server directly.
For example, some attackers utilize tools to uncover legacy DNS settings, potentially exposing the origin server’s IP address and permitting direct attacks on the origin server, bypassing WAF.To avoid this, make it a standard practice to assess the status of origin protection as part of your WAF configuration. Unlike many other leading WAF solutions where origin protection is optional, AppTrana distinguishes itself by enabling origin protection by default.



