Two separate campaigns have been stealing credentials and browsing history for months.

Credit: Getty Images
As many of us celebrated the year-end holidays, a small group of researchers worked overtime tracking a startling discovery: At least 33 browser extensions hosted in Google’s Chrome Web Store, some for as long as 18 months, were surreptitiously siphoning sensitive data from roughly 2.6 million devices.
The compromises came to light with the discovery by data loss prevention service Cyberhaven that a Chrome extension used by 400,000 of its customers had been updated with code that stole their sensitive data.
’Twas the night before Christmas
The malicious extension, available as version 24.10.4, was available for 31 hours, from December 25 at 1:32 AM UTC to Dec 26 at 2:50 AM UTC. Chrome browsers actively running Cyberhaven during that window would automatically download and install the malicious code. Cyberhaven responded by issuing version 24.10.5, and 24.10.6 a few days later.
The Cyberhaven extension is designed to prevent users from inadvertently entering sensitive data into emails or websites they visit. Analyses of version 24.10.4 showed that it was configured to work with different payloads that were downloaded from cyberhavenext[.]pro, a malicious site the threat actor registered to give the appearance it was affiliated with the company. One recovered payload, Cyberhaven said, scoured user devices for browser cookies and authentication credentials for the facebook.com domain. A separate payload recovered by security firm Secure Annex stole cookies and credentials for chatgpt.com; Cyberhaven said the payload didn’t appear functional.
Ars Video
How Lighting Design In The Callisto Protocol Elevates The Horror
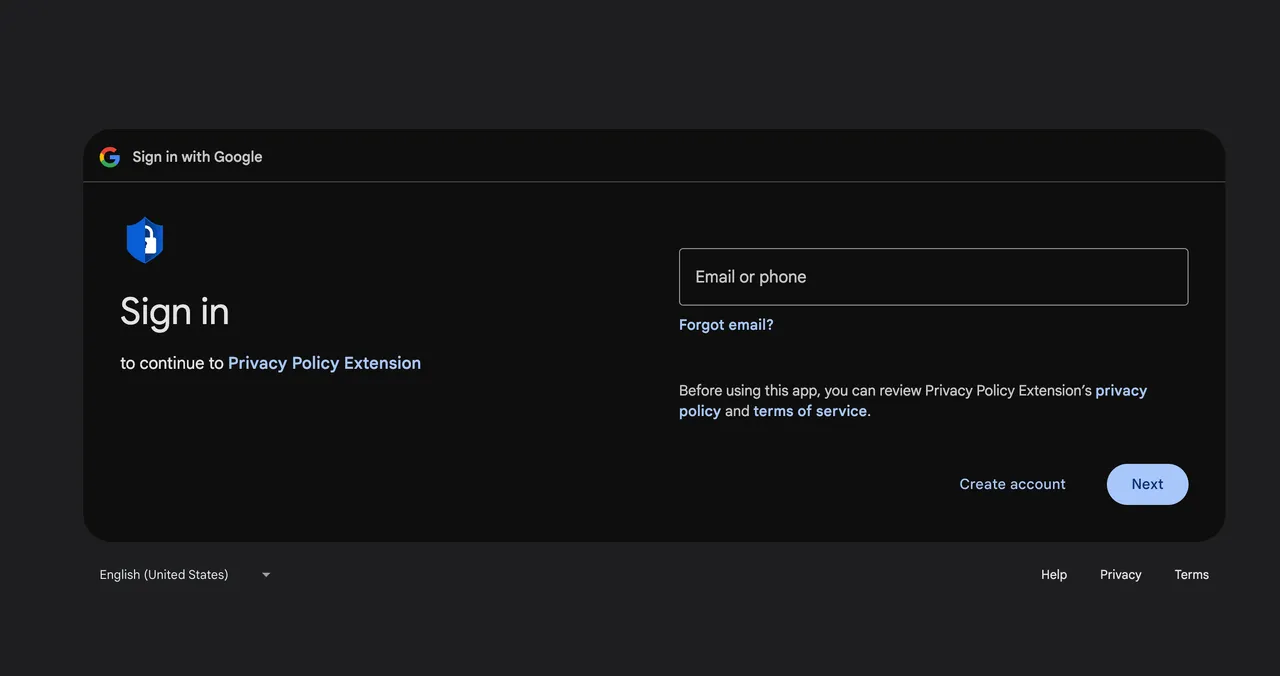
The malicious version came through a spear phishing email sent to the developers Google listed for the Cyberhaven extension on Christmas Eve. It warned that the extension wasn’t in compliance with Google terms and would be revoked unless the developer took immediate action.
A link in the email led to a Google consent screen requesting access permission for an OAuth application named Privacy Policy Extension. A Cyberhaven developer granted the permission and, in the process, unknowingly gave the attacker the ability to upload new versions of Cyberhaven’s Chrome extension to the Chrome Web Store. The attacker then used the permission to push out the malicious version 24.10.4.
As word of the attack spread in the early hours of December 25, developers and researchers discovered that other extensions were targeted, in many cases successfully, by the same spear phishing campaign. John Tuckner, founder of Secure Annex, a browser extension analysis and management firm, said that as of Thursday afternoon, he knew of 19 other Chrome extensions that were similarly compromised. In every case, the attacker used spear phishing to push a new malicious version and custom, look-alike domains to issue payloads and receive authentication credentials. Collectively, the 20 extensions had 1.46 million downloads.
“For many I talk to, managing browser extensions can be a lower priority item in their security program,” Tuckner wrote in an email. “Folks know they can present a threat, but rarely are teams taking action on them. We’ve often seen in security [that] one or two incidents can cause a reevaluation of an organization’s security posture. Incidents like this often result in teams scrambling to find a way to gain visibility and understanding of impact to their organizations.”
The earliest compromise occurred in May 2024. Tuckner provided the following spreadsheet:
| Name | ID | Version | Patch | Available | Users | Start | End |
| VPNCity | nnpnnpemnckcfdebeekibpiijlicmpom | 2.0.1 | FALSE | 10,000 | 12/12/24 | 12/31/24 | |
| Parrot Talks | kkodiihpgodmdankclfibbiphjkfdenh | 1.16.2 | TRUE | 40,000 | 12/25/24 | 12/31/24 | |
| Uvoice | oaikpkmjciadfpddlpjjdapglcihgdle | 1.0.12 | TRUE | 40,000 | 12/26/24 | 12/31/24 | |
| Internxt VPN | dpggmcodlahmljkhlmpgpdcffdaoccni | 1.1.1 | 1.2.0 | TRUE | 10,000 | 12/25/24 | 12/29/24 |
| Bookmark Favicon Changer | acmfnomgphggonodopogfbmkneepfgnh | 4.00 | TRUE | 40,000 | 12/25/24 | 12/31/24 | |
| Castorus | mnhffkhmpnefgklngfmlndmkimimbphc | 4.40 | 4.41 | TRUE | 50,000 | 12/26/24 | 12/27/24 |
| Wayin AI | cedgndijpacnfbdggppddacngjfdkaca | 0.0.11 | TRUE | 40,000 | 12/19/24 | 12/31/24 | |
| Search Copilot AI Assistant for Chrome | bbdnohkpnbkdkmnkddobeafboooinpla | 1.0.1 | TRUE | 20,000 | 7/17/24 | 12/31/24 | |
| VidHelper – Video Downloader | egmennebgadmncfjafcemlecimkepcle | 2.2.7 | TRUE | 20,000 | 12/26/24 | 12/31/24 | |
| AI Assistant – ChatGPT and Gemini for Chrome | bibjgkidgpfbblifamdlkdlhgihmfohh | 0.1.3 | FALSE | 4,000 | 5/31/24 | 10/25/24 | |
| TinaMind – The GPT-4o-powered AI Assistant! | befflofjcniongenjmbkgkoljhgliihe | 2.13.0 | 2.14.0 | TRUE | 40,000 | 12/15/24 | 12/20/24 |
| Bard AI chat | pkgciiiancapdlpcbppfkmeaieppikkk | 1.3.7 | FALSE | 100,000 | 9/5/24 | 10/22/24 | |
| Reader Mode | llimhhconnjiflfimocjggfjdlmlhblm | 1.5.7 | FALSE | 300,000 | 12/18/24 | 12/19/24 | |
| Primus (prev. PADO) | oeiomhmbaapihbilkfkhmlajkeegnjhe | 3.18.0 | 3.20.0 | TRUE | 40,000 | 12/18/24 | 12/25/24 |
| Cyberhaven security extension V3 | pajkjnmeojmbapicmbpliphjmcekeaac | 24.10.4 | 24.10.5 | TRUE | 400,000 | 12/24/24 | 12/26/24 |
| GraphQL Network Inspector | ndlbedplllcgconngcnfmkadhokfaaln | 2.22.6 | 2.22.7 | TRUE | 80,000 | 12/29/24 | 12/30/24 |
| GPT 4 Summary with OpenAI | epdjhgbipjpbbhoccdeipghoihibnfja | 1.4 | FALSE | 10,000 | 5/31/24 | 9/29/24 | |
| Vidnoz Flex – Video recorder & Video share | cplhlgabfijoiabgkigdafklbhhdkahj | 1.0.161 | FALSE | 6,000 | 12/25/24 | 12/29/24 | |
| YesCaptcha assistant | jiofmdifioeejeilfkpegipdjiopiekl | 1.1.61 | TRUE | 200,000 | 12/29/24 | 12/31/24 | |
| Proxy SwitchyOmega (V3) | hihblcmlaaademjlakdpicchbjnnnkbo | 3.0.2 | TRUE | 10,000 | 12/30/24 | 12/31/24 |
But wait, there’s more
One of the compromised extensions is called Reader Mode. Further analysis showed it had been compromised not just in the campaign targeting the other 19 extensions but in a separate campaign that started no later than April 2023. Tuckner said the source of the compromise appears to be a code library developers can use to monetize their extensions. The code library collects details about each web visit a browser makes. In exchange for incorporating the library into the extensions, developers receive a commission from the library creator.
Tuckner said that Reader Mode is one of 13 Chrome extensions known to have used the library to collect potentially sensitive data. Collectively, these extensions had 1.14 million installations. The full list is:
| Name | ID | Version | Patch | Available | Users | Start | End |
| Reader Mode | llimhhconnjiflfimocjggfjdlmlhblm | 1.5.7 | FALSE | 300,000 | 12/18/24 | 12/19/24 | |
| Tackker – online keylogger tool | ekpkdmohpdnebfedjjfklhpefgpgaaji | 1.3 | 1.4 | TRUE | 10,000 | 10/6/23 | 8/13/24 |
| AI Shop Buddy | epikoohpebngmakjinphfiagogjcnddm | 2.7.3 | TRUE | 4,000 | 4/30/24 | ||
| Sort by Oldest | miglaibdlgminlepgeifekifakochlka | 1.4.5 | TRUE | 2,000 | 1/11/24 | ||
| Rewards Search Automator | eanofdhdfbcalhflpbdipkjjkoimeeod | 1.4.9 | TRUE | 100,000 | 5/4/24 | ||
| Earny – Up to 20% Cash Back | ogbhbgkiojdollpjbhbamafmedkeockb | 1.8.1 | TRUE | 100,00 | 4/5/23 | ||
| ChatGPT Assistant – Smart Search | bgejafhieobnfpjlpcjjggoboebonfcg | 1.1.1 | TRUE | 189 | 2/12/24 | ||
| Keyboard History Recorder | igbodamhgjohafcenbcljfegbipdfjpk | 2.3 | TRUE | 5,000 | 7/29/24 | ||
| Email Hunter | mbindhfolmpijhodmgkloeeppmkhpmhc | 1.44 | TRUE | 100,000 | 9/17/24 | ||
| Visual Effects for Google Meet | hodiladlefdpcbemnbbcpclbmknkiaem | 3.1.3 | 3.2.4 | TRUE | 900,000 | 6/13/23 | 1/10/24 |
| ChatGPT App | lbneaaedflankmgmfbmaplggbmjjmbae | 1.3.8 | TRUE | 7,000 | 9/3/24 | ||
| Web Mirror | eaijffijbobmnonfhilihbejadplhddo | 2.4 | TRUE | 4,000 | 10/13/23 | ||
| Hi AI | hmiaoahjllhfgebflooeeefeiafpkfde | 1.0.0 | TRUE | 229 | 7/29/24 |
As Tuckner indicated, browser extensions have long remained a weak link in the security chain. In 2019, for example, extensions for both Chrome and Firefox were caught stealing sensitive data from 4 million devices. Many of the infected devices ran inside the networks of dozens of companies, including Tesla, Blue Origin, FireEye, Symantec, TMobile, and Reddit. In many cases, curbing the threat of malicious extensions is easy since so many extensions provide no useful benefit.
In the case of other abused extensions, such as the one used by Cyberhaven customers, it’s not as easy to address the threat. After all, the extension provides a service that many organizations find valuable. Tuckner said one potential part of the solution is for organizations to compile a browser asset management list that allows only selected extensions to run and blocks all others. Even then, Cyberhaven customers would have installed the malicious extension version unless the asset management list specifies a specific version to trust and to distrust all others.
Anyone who ran one of these compromised extensions should carefully consider changing passwords and other authentication credentials. The Secure Annex post provides additional indicators of compromise, as do posts here, here, here, and here.




