“Bootkitty” is likely a proof-of-concept, but may portend working UEFI malware for Linux.
Credit: Getty Images
UPDATE: November 28, 3:20 PM California time. The headline of this post has been changed. This update is adding the following further details: this threat is not a UEFI firmware implant or rootkit, it’s a UEFI bootkit attacking the bootloader. The Bootkitty sample analyzed by ESET was not unkillable. Below is the article with inaccurate details removed.
Researchers at security firm ESET said Wednesday that they found the first UEFI bootkit for Linux. The discovery may portend that UEFI bootkits that have targeted Windows systems in recent years may soon target Linux too.
Bootkitty—the name unknown threat actors gave to their Linux bootkit—was uploaded to VirusTotal earlier this month. Compared to many Windows UEFI bootkits, Bootkitty is still relatively rudimentary, containing imperfections in key under-the-hood functionality and lacking the means to infect all Linux distributions other than Ubuntu. That has led the company researchers to suspect the new bootkit is likely a proof-of-concept release. To date, ESET has found no evidence of actual infections in the wild.
Be prepared
Still, Bootkitty suggests threat actors may be actively developing a Linux version of the same sort of bootkit that previously was found only targeting Windows machines.
“Whether a proof of concept or not, Bootkitty marks an interesting move forward in the UEFI threat landscape, breaking the belief about modern UEFI bootkits being Windows-exclusive threats,” ESET researchers wrote. “Even though the current version from VirusTotal does not, at the moment, represent a real threat to the majority of Linux systems, it emphasizes the necessity of being prepared for potential future threats.”
Ars Video
What Happens to the Developers When AI Can Code? | Ars Frontiers
The Bootkitty sample ESET found is unable to override a defense, known as UEFI Secure Boot, that uses cryptographic signatures to ensure that each piece of software loaded during startup is trusted by a computer’s manufacturer. Secure Boot is designed to create a chain of trust that prevents attackers from replacing the intended bootup firmware with malicious firmware. When Secure Boot is enabled, if a single firmware link in that chain isn’t recognized, the device won’t boot.
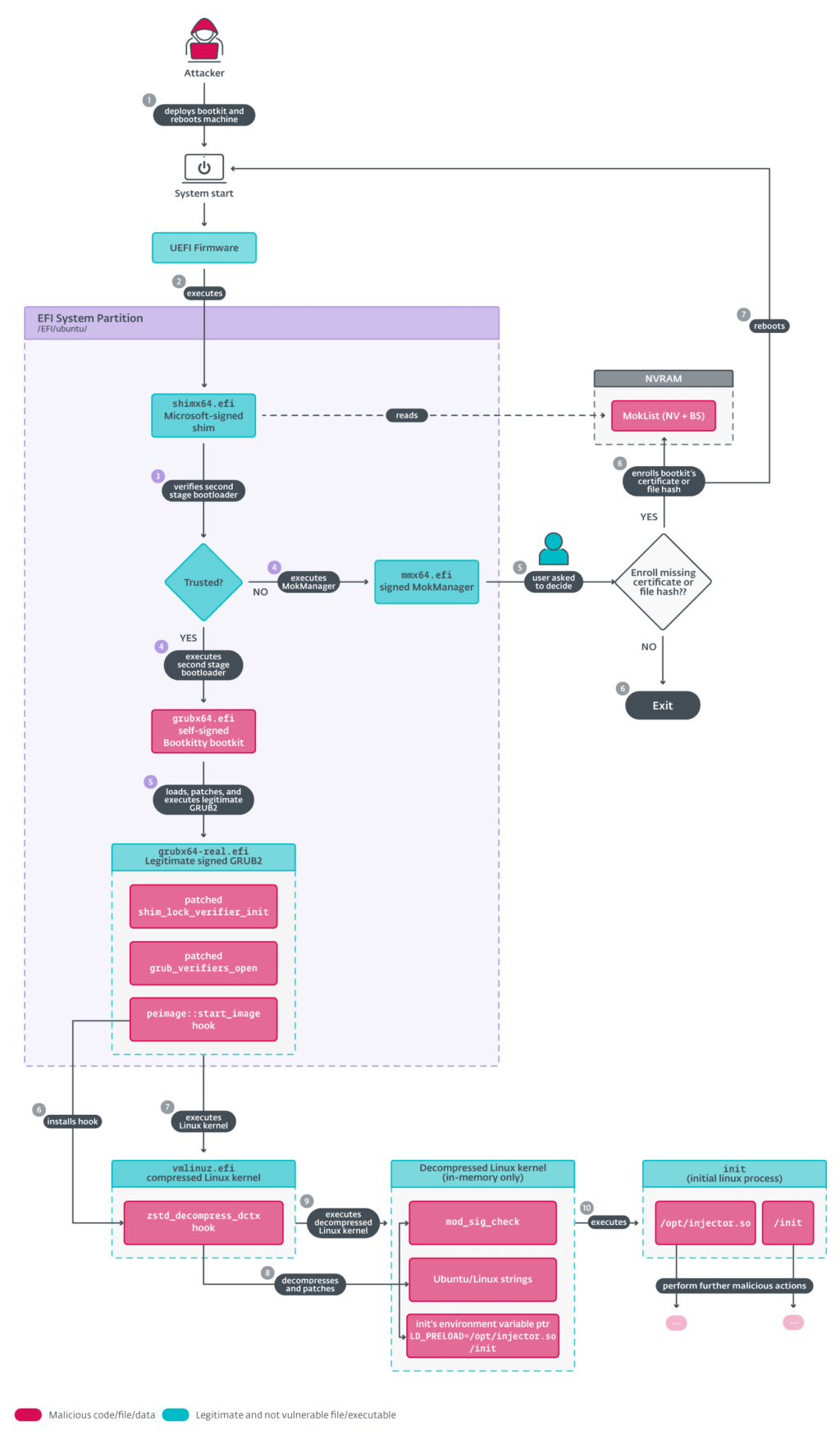
The image above summarizes the key parts of the Bootkitty execution flow. They are:
• Execution of the bootkit and patching of the legitimate GRUB bootloader (points 4 and 5 in Figure 6)
• Patching of the Linux kernel’s EFI stub loader (points 6 and 7 in Figure 6)
• Patching of the decompressed Linux kernel image (points 8 and 9 in Figure 6).
Despite working on a handful of Ubuntu versions, Bootkitty contains flaws and limitations in crucial functionality required for it to run on a wider based on machines. One imperfection resides in the way the bootkit modifies the decompressed Linux kernel. As shown in the chunk of Bootkitty code displayed below, once the kernel image is decompressed, Bootkitty simply copies the malicious patches to the hardcoded offsets within the kernel image.
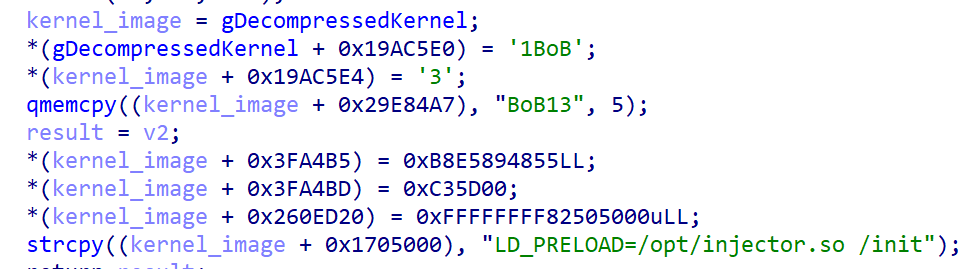
The result: “due to the lack of kernel-version checks in the function shown in [the figure above] Bootkitty can get to the point where it patches completely random code or data at these hardcoded offsets, thus crashing the system instead of compromising it,” ESET researchers explained.
Additionally, the inability to defeat Secure Boot may limit infection opportunities to devices that (1) don’t enable the defense or (2) have already been compromised by the same attacker to install a self-signed cryptographic certificate. Further, Bootkitty leaves a trail of artifacts behind that make discovery relatively easy. That undermines a key bootkit advantage: stealth.
As ESET notes, the discovery is nonetheless significant because it demonstrates someone—possibly a malicious threat actor—is pouring resources and know-how into creating working UEFI bootkits for Linux. Currently, there are few simple ways for people to detect compromised boot. The demand for these sorts of defenses will likely grow in the coming years.




